Likewise, users will have access to aliased files that reside outside the server root folder just as if they reside in a folder, also without the originals being at risk of hacking.
For example, the following Figure shows how aliased files and folders are served by Rumpus. In this example, the following directory structure is used:
\anonymous
\Users
\Bailey
\Chuck
\John
\Kenny
The "anonymous" directory is configured as the drop folder for the user
"ANONYMOUS" using Built-In Security. Additionally, each of the above users is
assigned his or her own folder as a drop folder, to which the user is restricted.
To allow access to the contents of the anonymous folder, an alias to the folder
is included in each of the user's drop folders. Figure 24 shows how this setup
appears in the Finder.
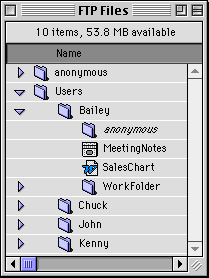
Figure 24: A hierarchical view of the FTP server's root folder.
The user named Bailey, for example, is dropped into the folder named Bailey and restricted to that folder. However, she has access to the anonymous directory via an alias. Figure 25 below shows exactly what Bailey will see when she logs in using Fetch.
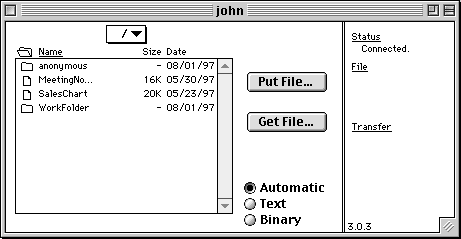
Figure 25: Aliased files and folders are fully supported in Rumpus.
Notice that, while she doesn't have access to Chuck, John, or Kenny's private folders, Bailey has complete access to the anonymous folder.
Copyright © 1997-9 Maxum Development Corporation
http://www.maxum.com/